What Is CMMC, and Why Should GovCons Care?
If you or your key subcontractors are still using a free, public email address, READ THIS ARTICLE.
If you think two-factor-authentication is a giant pain, and you can’t wait for it to go away, READ THIS ARTICLE.
If your corporate IT budget is dwarfed by your annually expensed meals, READ THIS ARTICLE.
If you think FEDRAMP is how the President’s dogs climb onto the White House sofa, READ THIS ARTICLE.
From the anticipated fallout of the Y2K bug to the more recent debilitating Colonial Pipeline hack, the security of our digital world is a worry. We worry about the theft of our credit card numbers, bank account numbers, even our identities; and for good reason. There is a lucrative market for these things.
The same is true for what the US federal government calls “Controlled Unclassified Information”, or “CUI”. CUI is broadly defined by the government, and depending on who you ask, it can be as significant as a document that fell just short of the criteria for “Classified” to something as trivial as a summary of a federal contract. Those interested in the list can see it here: CUI Categories | National Archives
In addition to defining CUI and creating rules compelling us to protect it, the government also worries that our widespread use of cloud computing has introduced security vulnerabilities, and CUI could fall into the wrong hands. This concern has prompted the launch of the “Cybersecurity Maturity Model Classification”, or “CMMC”.
DoD Leads the Way
It’s an old saying in the world of GovCon that one should look at what DoD is doing, as that will become the “standard” US Government-wide requirement in the years ahead. That is what we forecast for CMMC. CMMC, although in the headlines for the last few years, is a new requirement for Department of Defense (DoD) contractors. It’s how DoD certifies a contractor’s ability to protect the CUI and Federal Contract Information (FCI) that is in a Contractor’s possession.
DoD is planning to release an interim rule on the CMMC requirements by May 2023. One should expect that CMMC will be a DoD requirement this coming spring and that CMMC requirements will appear in contracts and solicitations by then. While the final requirements may still have to be worked out, CMMC is here to stay and it will apply to all DoD GovCons in the near term, regardless of size. Soon thereafter, we believe it will apply to all GovCons handling CUI and FCI.
Seriously, Though. What Does CMMC Have to Do With Me?
So, the elephant in the room, what is CMMC and why should GovCons care? CMMC is based on rules/practices established by the National Institute of Standards and Technology (NIST) to protect information from unauthorized access, and there are several reasons that GovCons should be paying attention.
There are three compliance tiers to the CMMC requirement as currently configured. The three tiers are: Foundation, Advanced, and Expert. The tier requirement will be called out in the solicitation based on the requirements of the contract and at the Contracting Officer’s discretion. Offerors must be certified at the solicitation’s tier to complete. Upon award, the GovCon will be responsible for assigning the appropriate certification tier to the work it plans to subcontract and making sure that the awarded subcontractor meets those requirements.
It is anticipated that the Level 1, or Foundation, requirement will be called out in 59.9% of the contract/subcontract requirements. Level 2, or Advanced, will be in 40% of the contract/subcontract requirement, while Level 3, or Expert, will be a requirement in 0.1% of the contracts. Clearly, any companies that want DoD business should focus on becoming compliant with Level 1 and Level 2, as that is where the preponderance of solicitations will fall.
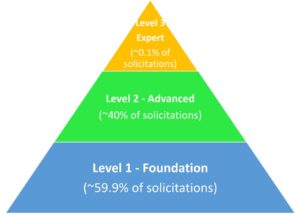
Beyond DoD, each GovCon should assume that in the near future some level of CMMC compliance will be a standard requirement in federal solicitations. Just like SAM registration is now a requirement for being a GovCon, so will some level of CMMC compliance.
Regulations aside, as a GovCon we have an inherent obligation to protect the information that is entrusted to us by the government. That is the essence of being a good corporate citizen and we know that GovCons strive to meet that standard.
Finally, and most importantly, we all are aware that there are bad actors in the world that would love to have direct access to US Government information, and who see the GovCon community as a means of easier access than trying to infiltrate the government directly. It is our collective responsibility to make those infiltrations as difficult as possible by having robust cyber security policies and procedures in place.
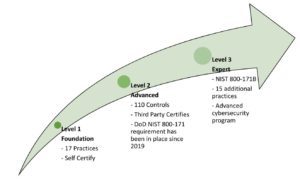
1-Foundation is, as the name implies, is a very basic or minimum level of cyber security required to hold Federal Contract Information (FCI). A level 1 or Foundation shows that a company has appropriate basic controls in place as part of their standard business processes to protect FCI. There are 17 required practices that a company must have in place to meet this requirement. Each company must self-certify their compliance to these 17 required practices. All GovCons should be operating at this level now.
2-Advanced is called out by the government when critical national security information is involved in the requirement. (Note this is different from classified information which has separate controls codified in the NISPOM.) At the advanced level, a company must show and demonstrate to a third party reviewer that they have their practices aligned with NIST SP 800-171. This standard covers 110 security controls that a company must have in place. These 110 security controls cover the 17 required practices at Level 1 and 93 additional practices detailed in the referenced NIST standard. A third party, not affiliated with the government, will assess each company’s policies, procedures, and practices to see if they are aligned and truly operational. Once a company has been assessed “compliant” to the Level 2, they must have their “status” reassessed by a third party on a triennial basis.
3-Expert is called out for DoD’s highest priority programs. Companies must comply with 110+ practices based on NIST 800-172B and be in full compliance with Level 2. At the Expert level, the government, not third parties, will perform this review. Rigorous policies and procedures must be in place.
The bottom line? All companies whose business is DoD based must get familiar now with CMMC and get compliant as soon as possible. This is not an overnight process that can be done at the last minute, and it is not inexpensive. For those companies whose business is not DoD based, while not a requirement now, expect it to become one soon. The watch word is, learn the CMMC requirements and get your company compliant.
This is coming your way. Contact your BOOST Contracts representative or [email protected] with any questions you may have about GovCon compliance.
ABOUT THE AUTHOR, KATHY WRIGHT
Kathy Wright is a contracts and procurement professional with more than 30 years of experience working with government and commercial contracts. She has worked for both small and large businesses and has developed a contracts management style that blends agility with process improvement.








